Major security flaw allows for impersonation of USC emails
External sender warning messages appears on many e-mail communications.
External sender warning messages appears on many e-mail communications.
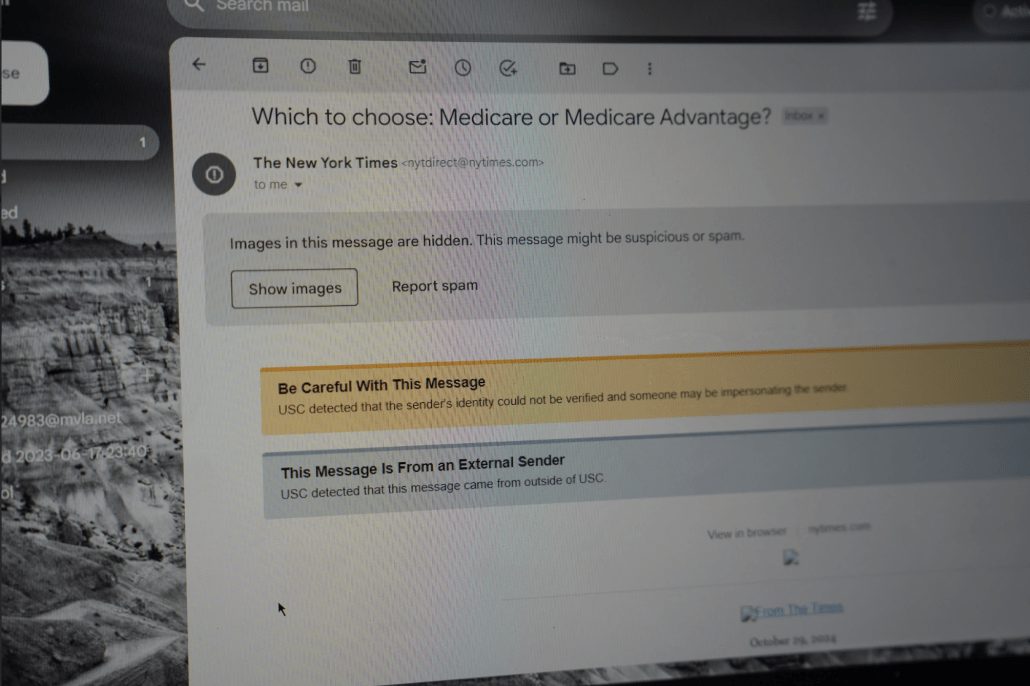
New email warning tags now show on many USC-affiliated emails after a large security flaw was discovered Oct. 18.
In a communitywide email Oct. 21, Information Technology Services acknowledged the warning tags but stated they were a product of Cybersecurity Awareness Month.
“In that spirit, we are making it easier to spot a potentially malicious email,” they wrote.
ITS said various warning tags will show depending on the email’s sender and recipient, and confirmed that emails from outside the University may be flagged.
The ITS email, ironically, was flagged as potentially suspicious because it was sent using an external email service. The system also flags any emails from non-USC addresses as suspicious, including Handshake and Mailchimp. Additionally, it flags emails from University-sponsored sources such as the Career Center.
Other banners may appear depending on the email. Messages include “someone may be impersonating the sender” and “you have not previously corresponded with this sender.” In certain cases, emails come with multiple warnings.
Several days earlier on Oct. 18, “Morning, Trojan,” a digital newsletter for USC students, uncovered a security issue that allows individuals to spoof USC accounts. Spoofing means disguising oneself as a trusted individual to access sensitive information.
“Morning, Trojan” was able to verify that various administrators can be spoofed, including President Carol Folt and Provost Andrew Guzman.
In all cases, the sender’s address and profile photos were impersonated, making the spoofed account virtually unidentifiable from the real account.
In certain cases, these emails would be marked as potential spam, but in all tested cases arrived in a recipient’s primary mailbox. A pattern based on administrative level was not apparent. For instance, some of Provost Guzman’s spoofed emails were marked as spam, but mail from President Folt’s spoofed account was not.
Tomoki Chien, one of the authors of the “Morning, Trojan” article, spoke with the Daily Trojan about the new email banners and said he disapproved of the security method.
“The banners are now flagging … things that are completely innocuous,” said Chien, a junior majoring in journalism. “[If anything] actually malicious were to land in your inbox, there is a lower chance that you will pay attention to that banner.”
Chien said “Morning, Trojan” reporters discovered the spoofing issue Friday, Oct. 18, and ITS was made aware of the problem that morning. The Universitywide email announcing new email banners was sent Oct. 21, but banners appeared the weekend prior.
In a statement to the Daily Trojan Oct. 28, ITS wrote they were aware of the spoofing issue and were actively working to resolve it.
“We were alerted to an email security concern and immediately engaged our information technology and cybersecurity teams, along with industry-leading partners,” ITS wrote. They did not comment on their progress toward resolving the problem, or whether the email banners were a result of the security concern.
ITS’s issues are not unique to USC. Many universities use outdated systems and email servers because an overhaul is resource- and time-intensive.
USC uses Simple Mail Transfer Protocol, which allows anyone on the internet to send emails to USC affiliates, not just those within the USC organization. However, its ease of access makes it accessible to spammers and spoofers. In modern times, SMTP’s security is often improved through filtering and security policies implemented by an organization.
Perhaps the most well-known example of an outdated system at USC is the Student Information System, which many students know as OASIS.
OASIS manages an enormous amount of student information, ranging from enrollment status to financial transactions. Because of its age, OASIS’ appearance is dated. However, the size and scope of such a system means overhauling it and fixing issues is a monumental task. This could necessitate portions of the system being offline for days or weeks.
Anya Jimenez, a junior majoring in writing for screen and television, said the new email banners will help the University community.
“Part of the way to fight [scammers and spoofers] is just making students and faculty … aware that there is a possibility for hacking and scams,” Jimenez said.
USC informs students about cybersecurity, ranging from courses in the Information Technology Program to emails from the Department of Public Safety warning about scams. However, issues such as spoofing serve as a reminder that people must express caution online, even when communications appear legitimate.
To Chien, the biggest surprise was how easily emails could be impersonated, with individuals needing only a computer and basic cybersecurity knowledge.
“You could spoof from a home network,” Chien said. “You don’t need a compromised email address … anybody can do it.”
Tomoki Chien was previously a photo editor at the Daily Trojan. Chien is no longer affiliated with the paper.
We are the only independent newspaper here at USC, run at every level by students. That means we aren’t tied down by any other interests but those of readers like you: the students, faculty, staff and South Central residents that together make up the USC community.
Independence is a double-edged sword: We have a unique lens into the University’s actions and policies, and can hold powerful figures accountable when others cannot. But that also means our budget is severely limited. We’re already spread thin as we compensate the writers, photographers, artists, designers and editors whose incredible work you see in our daily paper; as we work to revamp and expand our digital presence, we now have additional staff making podcasts, videos, webpages, our first ever magazine and social media content, who are at risk of being unable to receive the support they deserve.
We are therefore indebted to readers like you, who, by supporting us, help keep our paper daily (we are the only remaining college paper on the West Coast that prints every single weekday), independent, free and widely accessible.
Please consider supporting us. Even $1 goes a long way in supporting our work; if you are able, you can also support us with monthly, or even annual, donations. Thank you.
This site uses cookies. By continuing to browse the site, you are agreeing to our use of cookies.
Accept settingsDo Not AcceptWe may request cookies to be set on your device. We use cookies to let us know when you visit our websites, how you interact with us, to enrich your user experience, and to customize your relationship with our website.
Click on the different category headings to find out more. You can also change some of your preferences. Note that blocking some types of cookies may impact your experience on our websites and the services we are able to offer.
These cookies are strictly necessary to provide you with services available through our website and to use some of its features.
Because these cookies are strictly necessary to deliver the website, refusing them will have impact how our site functions. You always can block or delete cookies by changing your browser settings and force blocking all cookies on this website. But this will always prompt you to accept/refuse cookies when revisiting our site.
We fully respect if you want to refuse cookies but to avoid asking you again and again kindly allow us to store a cookie for that. You are free to opt out any time or opt in for other cookies to get a better experience. If you refuse cookies we will remove all set cookies in our domain.
We provide you with a list of stored cookies on your computer in our domain so you can check what we stored. Due to security reasons we are not able to show or modify cookies from other domains. You can check these in your browser security settings.
These cookies collect information that is used either in aggregate form to help us understand how our website is being used or how effective our marketing campaigns are, or to help us customize our website and application for you in order to enhance your experience.
If you do not want that we track your visit to our site you can disable tracking in your browser here:
We also use different external services like Google Webfonts, Google Maps, and external Video providers. Since these providers may collect personal data like your IP address we allow you to block them here. Please be aware that this might heavily reduce the functionality and appearance of our site. Changes will take effect once you reload the page.
Google Webfont Settings:
Google Map Settings:
Google reCaptcha Settings:
Vimeo and Youtube video embeds:
The following cookies are also needed - You can choose if you want to allow them:
